Microsoft Entra ID Protection Guide
Microsoft Entra ID Protection, formerly known as Azure Active Directory Identity Protection, assists organizations in detecting and responding to identity-based risks. It uses data from Microsoft’s vast threat intelligence network to identify suspicious user activities and sign-in patterns. For technical teams, properly configuring and using Identity Protection is key to preventing compromised identities and enforcing automated response actions.
This guide explains how to implement, monitor, and fine-tune Microsoft Entra ID Protection. It focuses on practical configurations, policy design, risk-based access controls, and advanced response techniques.
Understand Identity Risks in Microsoft Entra ID Protection
Before configuring any policies, it's important to understand the two main types of risks in Microsoft Entra ID Protection:
User Risk – Indicates a user account is likely compromised (e.g., leaked credentials, unusual activity).
Sign-in Risk – Flags suspicious login attempts (e.g., login from unfamiliar locations, atypical devices).
These risks are calculated using Microsoft’s machine learning models and updated continuously based on global telemetry. You can view detected risks from the Identity Protection pane in the portal or by querying Microsoft Graph APIs for automation.
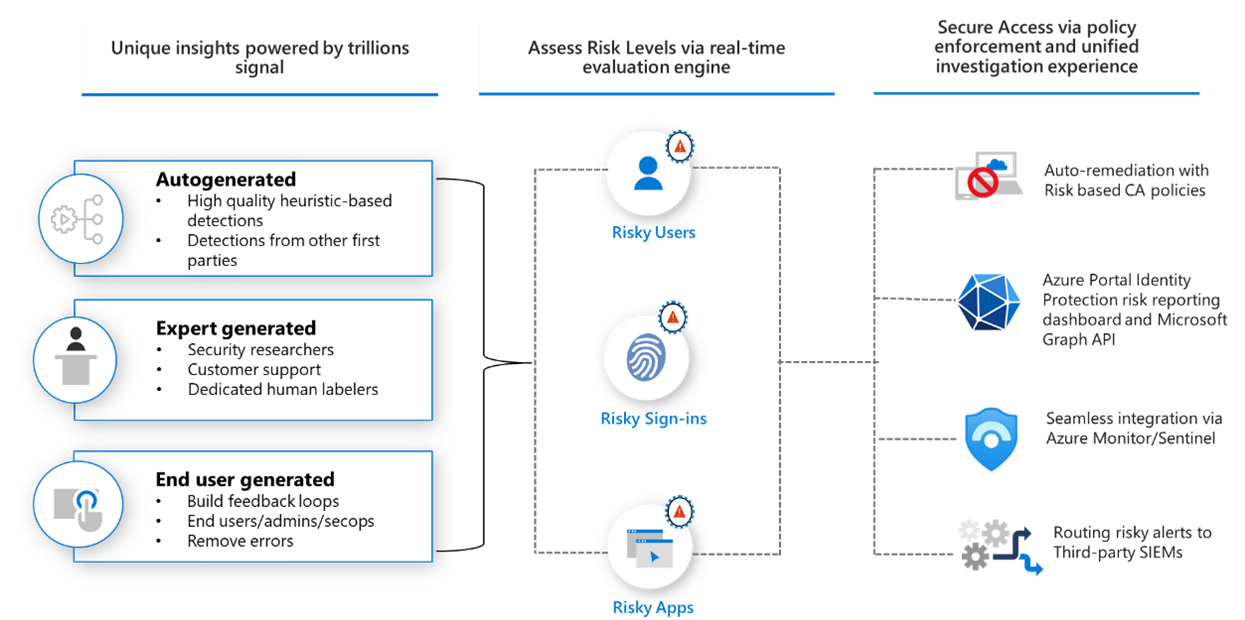
Microsoft Entra ID Protection dashboard displaying detected user and sign-in risks using machine learning to help secure identities and manage access policies.
Configure Risk Policies for Access Control
Once risks are detected, you can block or restrict access using Risk-Based Conditional Access policies. These policies can be configured to block access or enforce multi-factor authentication (MFA) if risk is detected.
Real-life Example: Block Access for High User Risk
This JSON configuration (via Microsoft Graph API) sets a Conditional Access policy that blocks sign-ins if user risk is high. In the portal, you can configure this visually under
Conditional Access > New Policy > User Risk.
Best Practices
Set high user risk = block access
Set medium sign-in risk = require MFA
Set low user risk = allow but monitor
Always test your policies with a small group before full deployment.

The Visual interface of Microsoft Entra ID Protection with risk-based access policies configured to block or restrict access based on user and sign-in risk levels.
Automate User Risk Remediation
Microsoft Entra ID Protection lets you automate responses for detected risks. If a user’s risk level reaches a certain threshold, you can trigger:
Password reset
MFA challenge
Account lockout
Access block
These responses are automatic when policies are enabled. You can also use custom workflows with Microsoft Graph Security API to trigger external tools or SIEM workflows.
Example: Reset Password on Risk Detection (Graph API)
This API call marks the user as compromised, which enforces a password reset and blocks access until resolved. Use this in logic apps, runbooks, or SIEM workflows to automatically respond to high-risk users.
Monitor Identity Protection Logs
Logs are crucial for visibility and response. Microsoft Entra ID Protection writes logs to:
Sign-in logs
Risky users
Risk detections
You can integrate logs into Log Analytics, Microsoft Sentinel or export to a SIEM.
Example KQL Query for Sentinel
This query identifies users with frequent high-risk sign-ins. Use this to prioritize investigation or refine risk policies.
Make sure diagnostic settings for Microsoft Entra ID are enabled and routed to your log destination.
Respond to False Positives
Machine learning models may produce false positives. Technical teams should:
Use Risk Dismiss to manually override risk if you confirm it's safe.
Investigate using correlated sign-in data, IP reputation, device compliance, and recent user activity.
Refine policies to reduce unnecessary user friction.
Risk dismissals can be done in the portal or with the Graph API:
Add audit logging to track overrides for security and compliance reasons.
Simulate and Test Identity Protection Policies
After setting up Identity Protection policies, it's critical to test their behavior before applying them organization-wide. This avoids accidental lockouts or unexpected access denials. Microsoft Entra ID provides multiple testing and simulation options that technical teams should use regularly to validate risk policies and access controls.
Testing helps ensure that policies:
Enforce the correct actions for specific risk levels
Do not block legitimate users
Work with existing MFA or hybrid identity configurations
Use the “What If” Tool for Conditional Access
Microsoft Entra ID’s built-in What If tool simulates how Conditional Access policies apply to a given user, location, device, or risk level.
Steps:
Go to Microsoft Entra ID > Security > Conditional Access > What If
Select a test user, location, platform, sign-in risk level, and app
Run the simulation to see which policies apply and what the result would be
This helps you validate your Identity Protection risk policies in the context of Conditional Access logic.
Test Risk Detection with Test Accounts
For real-world testing:
Use non-production test accounts.
Simulate high-risk sign-ins by logging in from unusual locations or using TOR/VPN (in a controlled environment).
Monitor the Risky sign-ins and Risky users’ reports to see how the risks are detected.
You can also use Microsoft’s Risky Sign-in Simulator to generate test signals.
Monitor Impact in Real-Time
After applying policies to a pilot group:
Use Sign-in logs to monitor access behavior
Check Risk detections to validate that policy thresholds are working as expected
Watch for increased MFA prompts or access blocks
Update your policy scope gradually—start with a few users or groups, validate logs, and expand in phases.
Conclusion
Microsoft Entra ID Protection is a great tool to minimize attacks based on identities. For the technical teams, merging automated policies, monitoring, and integrations can translate into proactive control of risky sign-ins and compromised users. Review your policies often; integrate them into your wider security operations; iterate your policies with relevant telemetry.
Think of this as never being set in stone. The procedure will always require evaluation, tuning, and validation. Every time it is set up properly, it establishes the foundation of your identity security posture.
REFERENCES
Last updated